
Application Security Without Compromise
Thousands of web assets to secure? No problem.
Accuracy
Find the vulnerabilities other tools miss »
Visibility
See the complete picture of your app security »
Automation
Automate security throughout your SDLC »

Accuracy
Find the vulnerabilities other tools miss
Head-to-head tests by independent researchers show that Invicti consistently identifies more vulnerabilities than other scanning tools. And returns fewer false positives.
- Find more true vulnerabilities with our unique dynamic + interactive (DAST + IAST) scanning approach.
- Let no vulnerability go unnoticed with combined signature and behavior-based testing.
- Detect vulnerabilities quickly with comprehensive scanning that doesn’t sacrifice speed or accuracy.

Visibility
See the complete picture of your app security
Without complete visibility into your customers’ apps, vulnerabilities, and remediation efforts, it’s impossible to prove they’re doing everything they can to reduce their company’s risk.
- Find all web assets — even ones that have been lost, forgotten, or created by rogue departments.
- Scan the corners of apps that other tools miss with Invicti’s unique dynamic + interactive (DAST + IAST) scanning approach.
- Always know the status of remediation efforts, through Invicti or native integrations with issue tracking and ticketing software.
Automation
Automate security throughout your SDLC
Security challenges grow faster than their teams. That’s why customers need security testing automation built into every step of their SDLC.
- Automate security tasks and save hundreds of hours each month.
- Identify the vulnerabilities that really matter — then seamlessly assign them for remediation.
- Help security and development teams get ahead of their workloads — whether they run an AppSec, DevOps, or DevSecOps program.
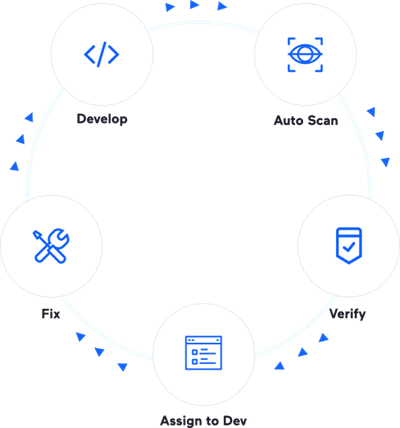
5 Steps to Secure Applications
There’s no such thing as “100% secure”.
Here’ how Invicti gives you the next best thing.
Build Security automation into every step of your customers’ SDLC so they can get more security with less manual effort.
Invicti’s 5 Steps to Secure Applications
Step 1:
Discover & Crawl
Step 2:
Detect
Step 3:
Resolve
Step 4:
Integrate
Step 5:
Continuously Secure
Step 1:
Discover & Crawl All Assets
Forgotten and outdated web applications are often targeted by attackers to gain an entry point into the organization. Invicti Enterprise uses a proprietary continuous web asset discovery engine to automatically identify all your customers’ websites and web applications. Discovery covers all their web-facing assets, whether legacy or modern, and any future additions are automatically detected and reported.
Step 2:
Detect Vulnerabilities
Find more vulnerabilities with the industry’s best DAST+IAST solution, developed with the same team that pioneered interactive scanning a decade ago. When enabled, the Invicti Shark IAST module can detect additional vulnerabilities in the application environment and provide an extra layer of detail for many other results. By combining Proof-Based Scanning with IAST, Invicti Enterprise delivers fast, accurate, and highly detailed results.
Step 3:
Resolve Issues
Shrink security backlog by eliminating the noise and uncertainty that false positives bring into remediation workflows. Invicti uses proprietary Proof-Based Scanning technology to automatically confirm the majority of exploitable vulnerabilities and assign a severity rating. Vulnerability reports for developers include detailed issue information complete with the potential impact and remediation guidelines. For many popular web technologies, the additional IAST module can even provide a specific line number or stack trace for faster and more effective fixes.
Step 4:
Integrate Security into Development
Eliminate security bottlenecks and streamline security issue resolution by creating a closed-loop security solution. Invicti Enterprise includes out-of-the-box integrations with popular CI/CD platforms and issue trackers, including Jenkins and Jira, to automatically trigger scans, create developer tickets for vulnerabilities, and retest submitted fixes. With proven and actionable vulnerability reports delivered straight into the developers’ existing workflows, you can your customers hundreds of man-hours on manual security management and efficiently fix security issues before they make it into production.
Step 5:
Continuously Secure
Cybercriminals don’t operate on a fixed schedule, so their security shouldn’t, either. To automate security testing while keeping up with the rapid pace of modern web development, it needs to be built into the development and operations process itself. With Invicti, your customers can automatically feed trustworthy and actionable vulnerability scan results directly into their software development lifecycle (SDLC) to minimize security risks without delaying new features and releases. To stay protected against new attacks, they can also schedule recurring scans for applications already in production.
 Please Wait...
Please Wait...